Booting in Safe Mode in Windows 8 and 8.1
Booting in safe mode in windows 8 and 8.1 simply do not work by just pressing the F8 button while booting because the boot process is so fast it cannot detect any keystrokes made along the process. But do not worry about it because I am here to save you and will boot the PC right away without further ado. This process do not take a master to learn and do not need any special software to perform.
The following are the best and easiest two methods on booting in Safe Mode. Get Safe Mode without the following:
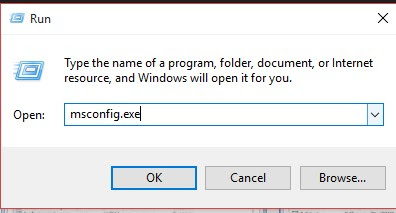
Method 1 – Using MSCONFIG.exe
Method 2 – Using Shift + Restart
- The second and a very simple method is by pressing the Power Button and holding theShift Key on your keyboard and click on “Restart” Button
- Windows will give more additional options when so, simply click on the Troubleshootoption.
- Then go to Advanced Options.
- Lastly, Press Startup Settings. Your PC will restart under safe mode options. Just click onRestart.
- After restart you will need to choose among the available options from F1 to F9 to what boot to perform since this tutorial is for safe mode then click on F4.
- Viola! You are done!